The evolution of security incident and event management (SIEM) or: using smart data analysis to create a big data security intelligence (BDSI) system
State-of-the-art SIEM systems are designed to detect and report security-relevant incidents from a large amount of data using prescribed analysis tools. However, their effectiveness depends to a great extent on how they are planned and installed, which can also be said of many complex issues. But in this field, a very wide range of varying expertise is required. Shortcomings in one area quickly make a SIEM system expensive and you’ll also reduce the benefits that you could theoretically gain from the system as well as impact the future viability of the landscape.
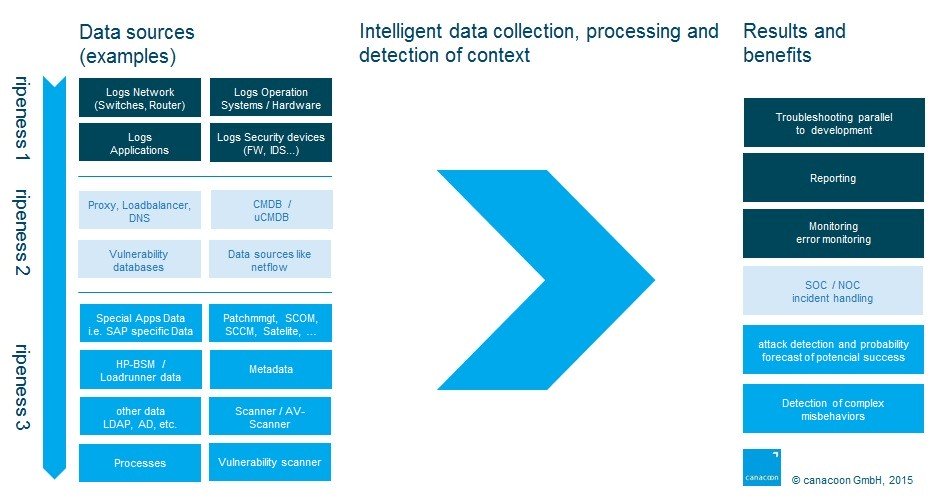
To set up a SIEM system properly and to advise customers as independently as possible about future-proof solutions, considerable knowledge is needed: As well as product-specific skills, expertise concerning attackers and processes – for example, incident processes and their requirements (sometimes in an international context) – is a must. In modern environments, data mining experience is also crucial. This experience serves as the basis for broadening the classic SIEM system from rule-based or pattern-based recognition to the recognition of correlations from mass data analyses using many different sources by deploying mathematical algorithms. canacoon refers to this as BIG DATA SECURITY INTELLIGENCE – or BDSI for short.
But why should companies start thinking about BIG DATA SECURITY INTELLIGENCE (BDSI), when all they’re tasked with is setting up a SIEM system? The answer is simple. Attackers adjust their behavior fast, meaning that you need to catch up quickly and make changes. Self-learning systems that learn from their own data and can recognize correlations can even be used to forecast attacks, putting them in the top class of data mining tools. But you’ll need more than just a SIEM system. Your IT architectures and systems must be enabled and extensible, ensuring optimal investment protection. An appropriate data mining background is therefore indispensable.
We are happy to advise you and empower you to determine the probability of attacks on your systems and to take proactive action.
Background
Even creative hackers use some kind of logic in their attacks. There are dependencies and sequences that need to be observed to make an attack work. However, these vary according to context and they change constantly. Furthermore, target systems also change and are suddenly identified as vulnerable as soon as a security gap becomes apparent. One of the objectives of BIG DATA SECURITY INTELLIGENCE (BDSI) is to establish a connection between all this data.
Attackers are always a step ahead. But you can reduce the distance significantly and efficiently.
Self-learning systems that can detect interrelations enable potential or current risks to be traced in a targeted way.